最新发布|DACS-Gaming游戏行业解决方案重磅升级
了解更多Innovative Kernel-Level Secure Workspace
DACS adopts kernel-level security sandbox technology to create one or more independent secure workspaces on a terminal device that are isolated from the local environment and managed by the enterprise, with comprehensive isolation and control from data reading and writing, clipboard, external device connection, printing interface, etc., so as to achieve the effect of data isolation in the secure workspace and prohibit end-users from leaking data information out of the security workspace in any way. Moreover, DACS stores all data inside designated high-strength encrypted disk space, allowing only the authorized applications in the secure workspace – and no other applications outside the secure workspace – to read enterprise data.
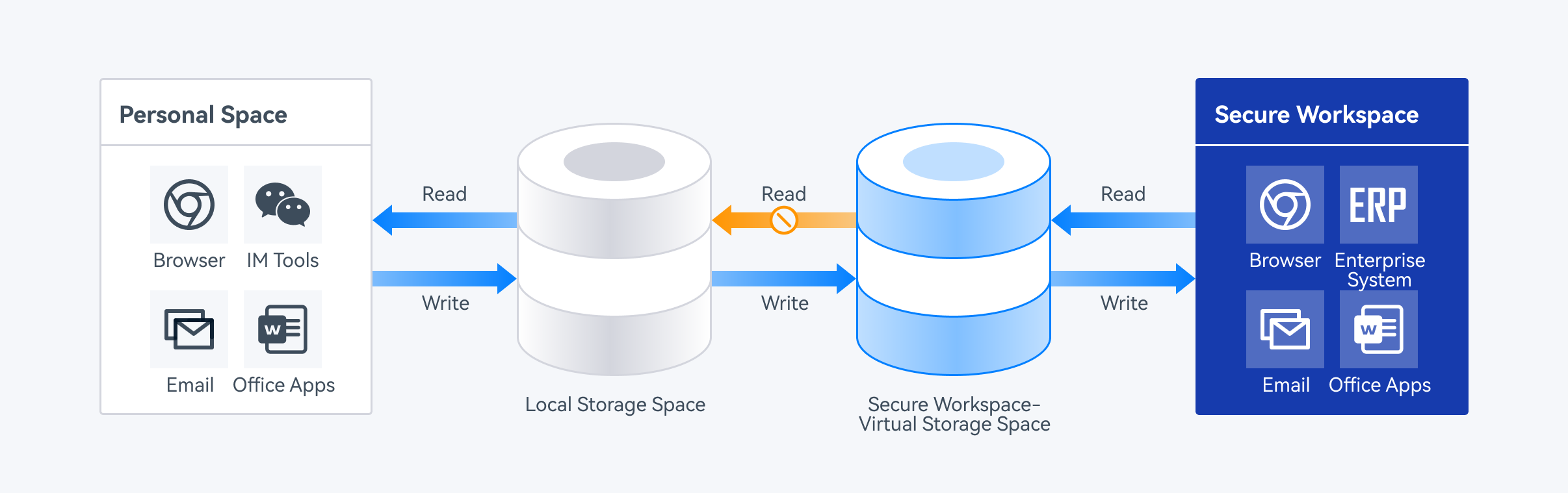
Data read/write control
DACS Pro redirects all data created inside secure workspace to designated virtual storage spaces by default, where only the authorized applications running in this secure space can read the data. Applications inside personal workspace interact normally with the local disk and cannot read or write data of the secure workspace, i.e., it is impossible to access, search, or modify any data inside the secure workspace.
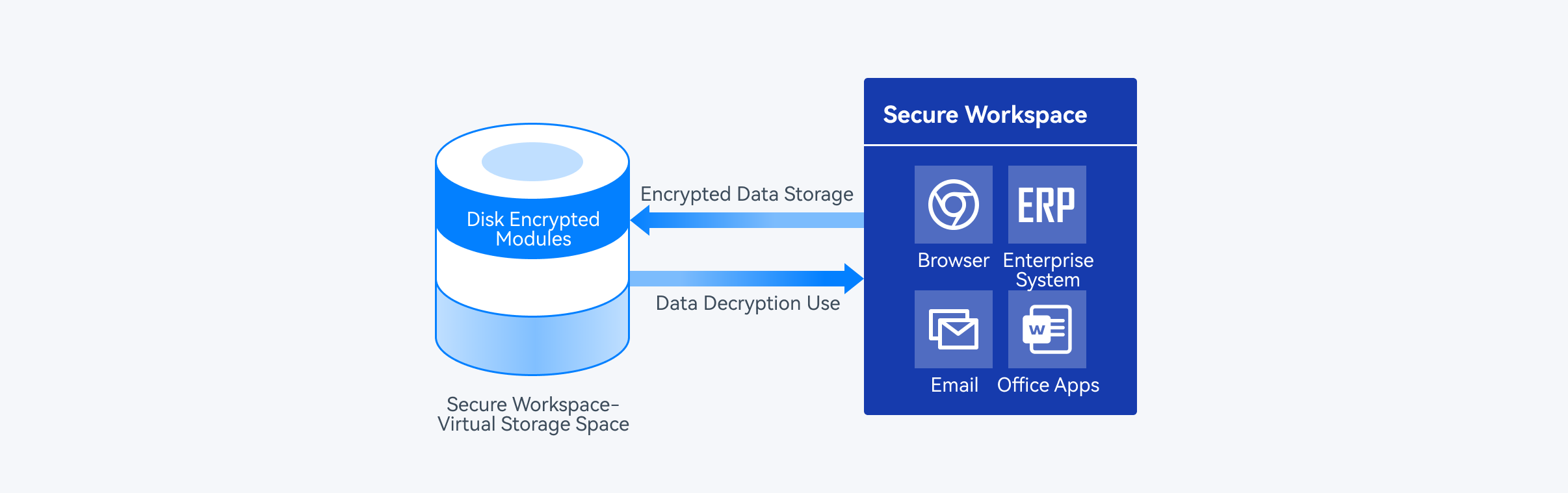
Encrypted data storage
Through disk encryption, DACS Pro uses AES256 high-strength encryption algorithm to encrypt the entire virtual storage space created by the secure workspace, building encryption modules on its outer layers. Encryption modules encrypt all data read and write operations before they are stored in the virtual storage space under the workspace-designated path. This way, whether creating, downloading, or receiving outside documents in the secure workspace, documents are automatically stored in an encrypted virtual environment.
Isolated inter-process communication
DACS Pro supports process isolation inside and outside the secure workspace, blocking communication between processes inside and outside the workspace, protecting processes running in the secure workspace from outside interference, and preventing enterprise data leakage, including but not limited to: isolation of various types of IPC, COM interfaces, network communication, messages, registries and other communication ways.
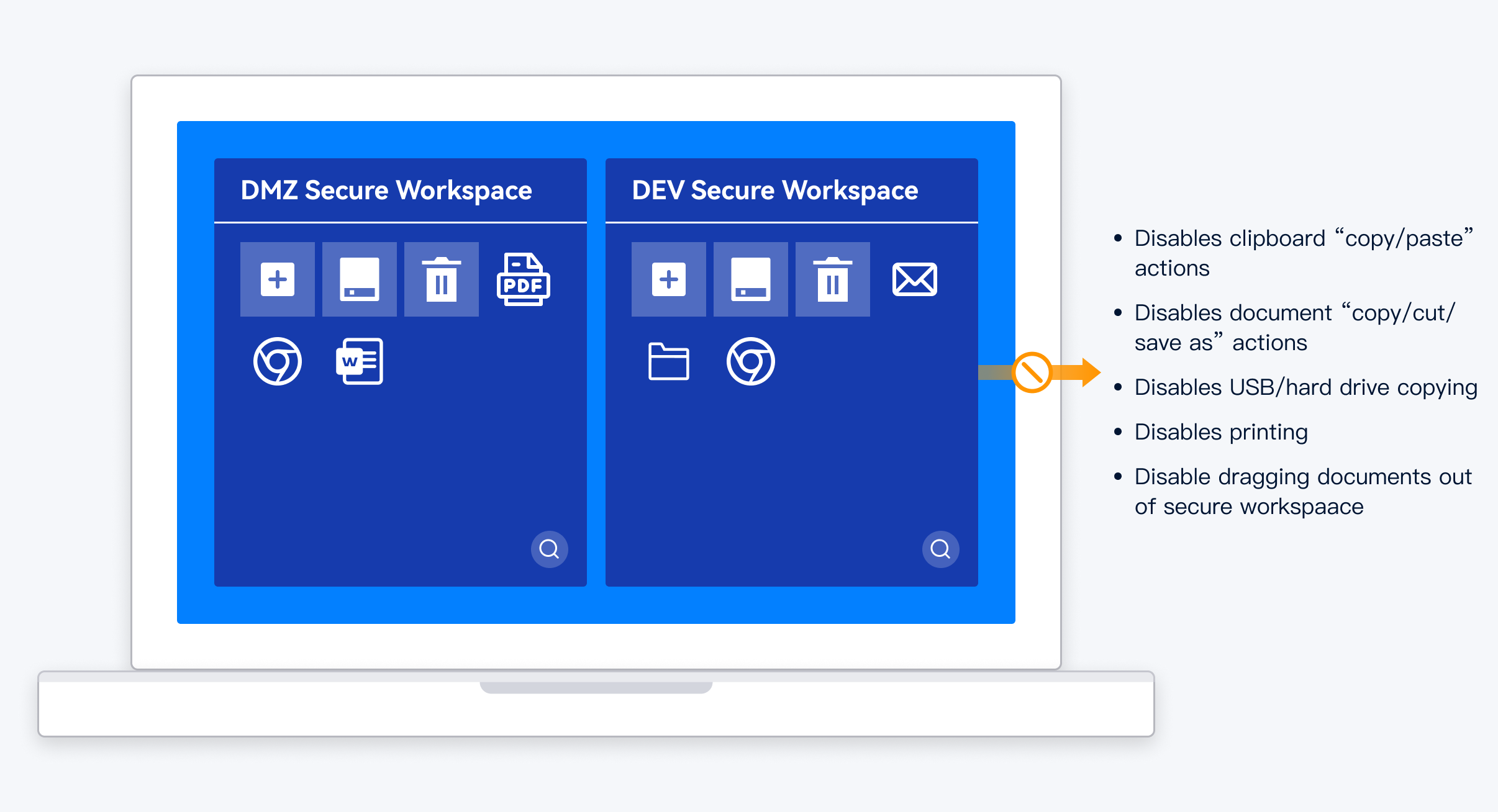
Clipboard control
DACS Pro supports flexible control of clipboard operations in the secure workspace, clipboard operations in the secure workspace are blocked and isolated by default, and end-users cannot be able to copy text or images from the secure workspace to their personal workspace.
Print control
Printing is one of the common ways of data leakage, and DACS Pro supports blocking the printing of documents in the secure workspace. However, considering how printing is an essential need in everyday work, DACS Pro also supports printing approved documents with automatic watermarks while uploading print content to the backend for audit.
External device connection control
External devices with no leakage risks are accepted for use in secure workspaces, foEr example, mice, keyboards, pen tablets, headphones, audio and microphones.
External devices with leakage risks can be granted/denied connection through the settings, for example, USB flash drives, mobile disks, burners, etc. In addition, MTP, ADB and other transmission protocol level controls are also supported.
Offline access control
When the secure workspace is offline due to changes in the network environment, the administrator can flexibly set to allow designated users to use the data in the designated secure workspace offline and the duration of use.
If offline access is restricted, then the secure workspace locks once offline, and there exists no possible means of accessing the data inside, including physically destroying the terminal devices and directly reading the original data on the disk, protecting the enterprise data from being stolen under any circumstances.
Innovative Kernel-Level Secure Workspace
DACS adopts kernel-level security sandbox technology to create one or more independent secure workspaces on a terminal device that are isolated from the local environment and managed by the enterprise, with comprehensive isolation and control from data reading and writing, clipboard, external device connection, printing interface, etc., so as to achieve the effect of data isolation in the secure workspace and prohibit end-users from leaking data information out of the security workspace in any way. Moreover, DACS stores all data inside designated high-strength encrypted disk space, allowing only the authorized applications in the secure workspace – and no other applications outside the secure workspace – to read enterprise data.

Data read/write control
DACS Pro redirects all data created inside secure workspace to designated virtual storage spaces by default, where only the authorized applications running in this secure space can read the data. Applications inside personal workspace interact normally with the local disk and cannot read or write data of the secure workspace, i.e., it is impossible to access, search, or modify any data inside the secure workspace.

Encrypted data storage
Through disk encryption, DACS Pro uses AES256 high-strength encryption algorithm to encrypt the entire virtual storage space created by the secure workspace, building encryption modules on its outer layers. Encryption modules encrypt all data read and write operations before they are stored in the virtual storage space under the workspace-designated path. This way, whether creating, downloading, or receiving outside documents in the secure workspace, documents are automatically stored in an encrypted virtual environment.

Isolated inter-process communication
DACS Pro supports process isolation inside and outside the secure workspace, blocking communication between processes inside and outside the workspace, protecting processes running in the secure workspace from outside interference, and preventing enterprise data leakage, including but not limited to: isolation of various types of IPC, COM interfaces, network communication, messages, registries and other communication ways.
Clipboard control
DACS Pro supports flexible control of clipboard operations in the secure workspace, clipboard operations in the secure workspace are blocked and isolated by default, and end-users cannot be able to copy text or images from the secure workspace to their personal workspace.
Print control
Printing is one of the common ways of data leakage, and DACS Pro supports blocking the printing of documents in the secure workspace. However, considering how printing is an essential need in everyday work, DACS Pro also supports printing approved documents with automatic watermarks while uploading print content to the backend for audit.
External device connection control
External devices with no leakage risks are accepted for use in secure workspaces, foEr example, mice, keyboards, pen tablets, headphones, audio and microphones.
External devices with leakage risks can be granted/denied connection through the settings, for example, USB flash drives, mobile disks, burners, etc. In addition, MTP, ADB and other transmission protocol level controls are also supported.
Offline access control
When the secure workspace is offline due to changes in the network environment, the administrator can flexibly set to allow designated users to use the data in the designated secure workspace offline and the duration of use.
If offline access is restricted, then the secure workspace locks once offline, and there exists no possible means of accessing the data inside, including physically destroying the terminal devices and directly reading the original data on the disk, protecting the enterprise data from being stolen under any circumstances.
Contact Us