最新发布|DACS-Gaming游戏行业解决方案重磅升级
了解更多Native Operation, Ultimate Experience
Moving workspaces in a one-click process
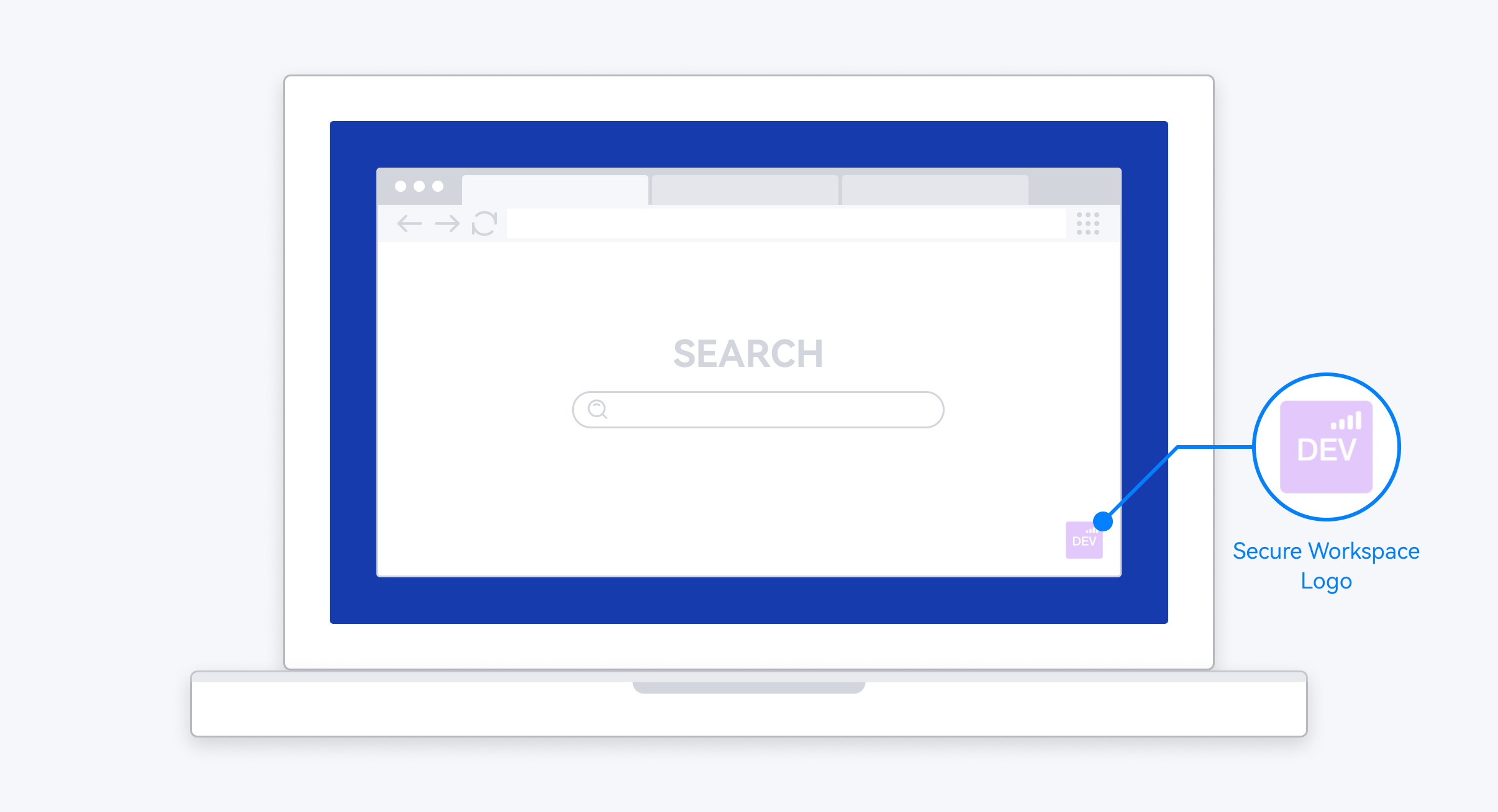
Users only need to drag the application shortcut on their personal desktop into the secure workspace to complete the movement of applications from the personal workspace to the secure workspace, and can double-click the application icon in the secure workspace to open and run directly, without reinstalling any applications in the secure workspace, realizing fast and convenient application movement and use.

All applications running in the secure workspace add the corresponding secure workspace logo to enhance the distinctiveness of enterprise security applications.
Enterprise-personal data separation
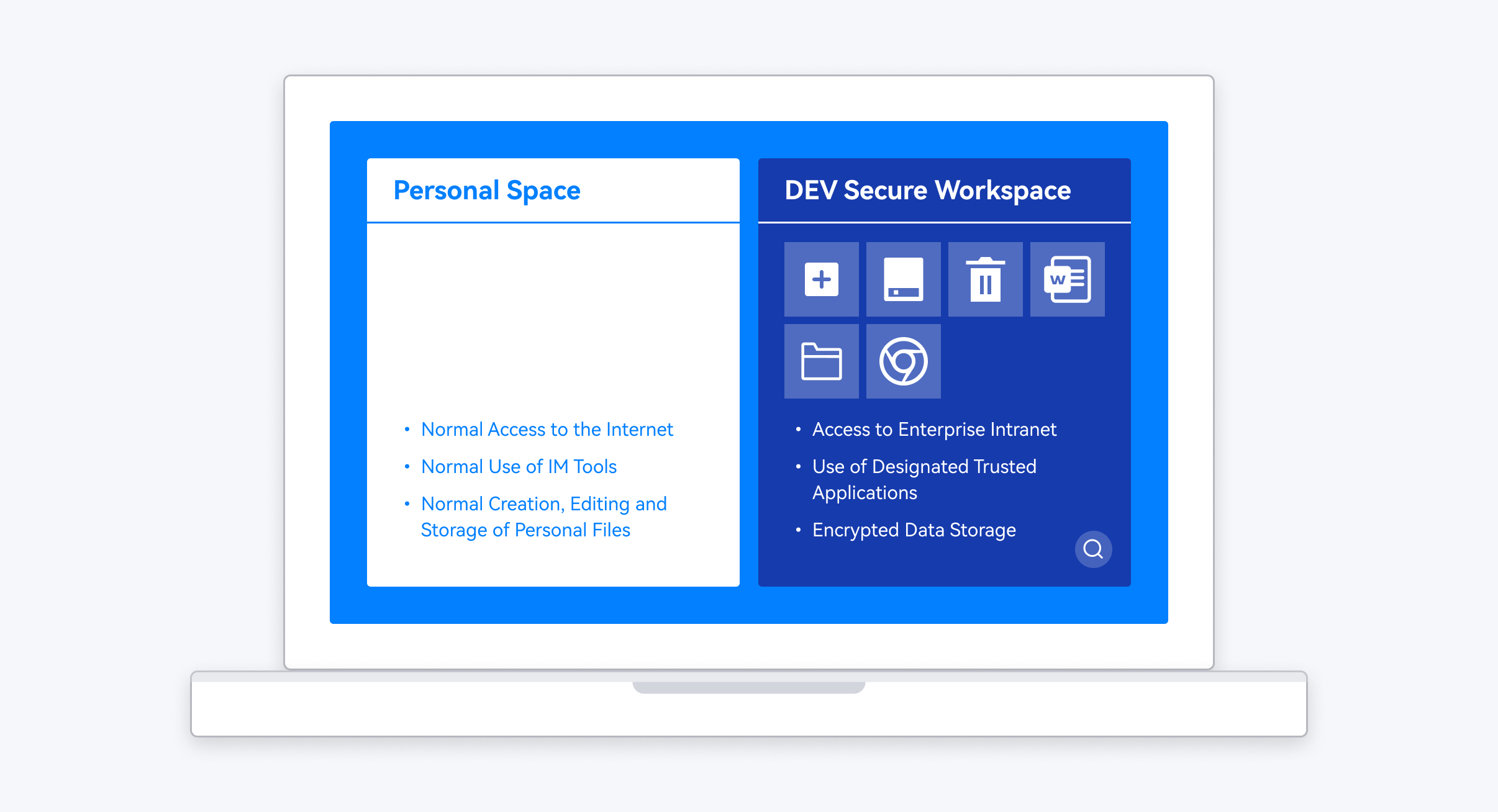
In an environment with clear isolated boundaries, ensure that personal data stored in the local environment will not be violated, avoid mixing all data, achieve a clear distinction between enterprise data and personal data, protect personal privacy, and ease enterprise management and employees' use.
Fully compatible
Support mainstream operating systems such as Windows, macOS, Linux, Android, iOS, etc., and keep consistent with the operating habits of native systems, without additional learning by employees.

Visualization and unified management
After one-click installation of the terminal, the administrator can visually manage the employees, equipment, secure workspaces and security policies of the enterprise through the friendly graphical interface of the administrative console.
Native Operation, Ultimate Experience
Moving workspaces in a one-click process
Users only need to drag the application shortcut on their personal desktop into the secure workspace to complete the movement of applications from the personal workspace to the secure workspace, and can double-click the application icon in the secure workspace to open and run directly, without reinstalling any applications in the secure workspace, realizing fast and convenient application movement and use.

All applications running in the secure workspace add the corresponding secure workspace logo to enhance the distinctiveness of enterprise security applications.

Enterprise-personal data separation
In an environment with clear isolated boundaries, ensure that personal data stored in the local environment will not be violated, avoid mixing all data, achieve a clear distinction between enterprise data and personal data, protect personal privacy, and ease enterprise management and employees' use.

Fully compatible
Support mainstream operating systems such as Windows, macOS, Linux, Android, iOS, etc., and keep consistent with the operating habits of native systems, without additional learning by employees.

Visualization and unified management
After one-click installation of the terminal, the administrator can visually manage the employees, equipment, secure workspaces and security policies of the enterprise through the friendly graphical interface of the administrative console.
Contact Us